Table Of Contents
What Level Of System And Network Configuration Is Required For CUI?
If you were curious about the depth of system and network configuration necessary for CUI, you would be in good company.
Controlled Unclassified Information (CUI) is no different from any other piece of technical jargon.
It is a new concept that implies real-world accountability for organizations that handle sensitive government-related data.
In fact, whether you are a federal contractor, a small business that is working on defense projects, or a company that deals with government data indirectly.
This includes understanding the specific system and network requirements of CUI, which is the first step to obtaining the correct answer.
Unlike general data security practices, CUI compliance requires a higher level of design, supervision, and technical protection.
Every aspect of your IT infrastructure, including encryption and user access, must be carefully coordinated and properly maintained.
To start with, CUI, the primary reason is that your organization becomes necessary—moreover, the type of setup your organization requires to remain secure and compliant.
What Is CUI And Why Does It Matter?

Controlled Unclassified Information refers to data that is not classified for national security purposes but still requires safeguarding in accordance with federal law.
In fact, these data acts as the “middle ground” between publicly available information and top-secret government files.
This can include legal documents, technical drawings, export-controlled data, and sensitive financial records.
Both the U.S. Federal Government and the Department of Defense (DoD) have established CUI standards to protect data from unauthorized access or disclosure.
If your company handles CUI, you must comply with the law and follow very detailed instructions to keep it secure whether it is storing, transmitting, or processing it.
This is what makes the issue of system and network configuration not only a theoretical question.
But it is also a matter of creating a virtual bastion. It protects the data considered by the government to be of utmost importance.
The Framework And Standards Of CUI
To protect CUI, organizations have to implement specific security measures as laid out by the National Institute of Standards and Technology (NIST).
The primary framework is NIST SP 800-171, a comprehensive guidance document that outlines how Controlled Unclassified Information should be protected in non-federal systems.
This particular framework is centered on the CIA triad, which comprises Confidentiality, Integrity, and Availability.
So, the framework implies that your system should not only maintain the confidentiality of the data.
Instead, it also ensures that the data remains accurate and accessible to users with the appropriate rights when required.
NIST SP 800-171 specifies the control families that encompass the individual security requirements.
There are fourteen security families in the standard, ranging from access control to risk assessment, that have been addressed within system security requirements.
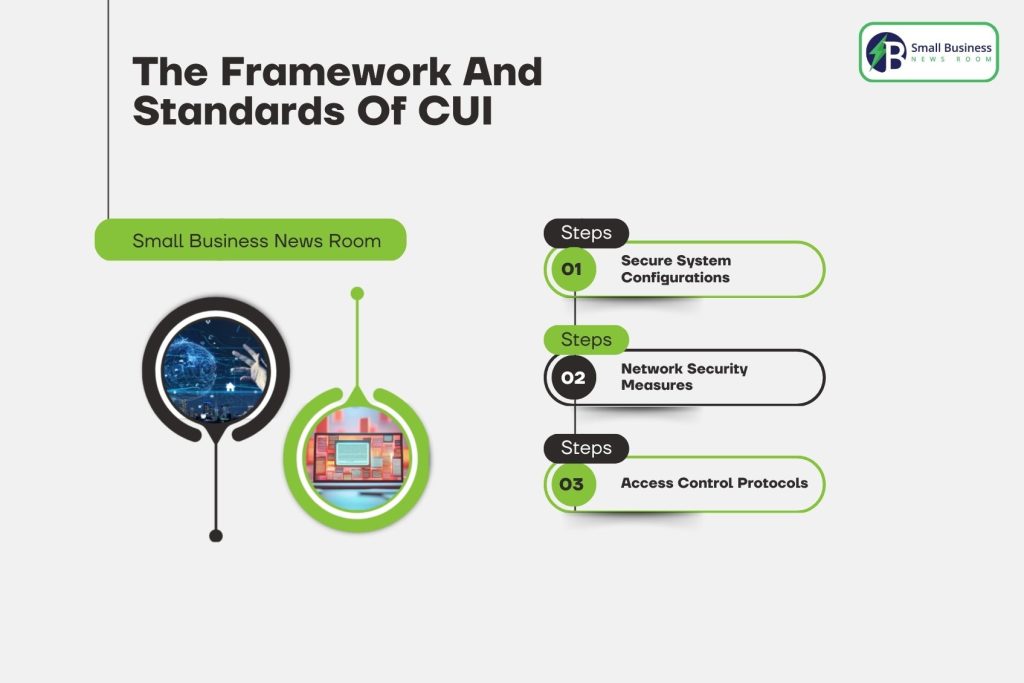
Now, it is technical. For NIST compliance, organizations need to have:
Secure System Configurations: Included here are the operating systems that have undergone the hardening process, the established security baseline, and the restricted administrative privileges.
Network Security Measures: These include encrypted communication channels (TLS/SSL or VPNs), an intrusion detection system, and firewall-protected networks that one can use to isolate sensitive data.
Access Control Protocols: In addition to multi-factor authentication, the strict management of user permissions and ICP is crucial. It also helps in keeping logs of every access attempt to establish an audit trail.
They are not optional features added to the system. Rather, they form part of the baseline requirements for personnel who deal with CUI.
What Kind Of Business Requirement Do You Need To Handle CUI?
So, let’s say you are a defense contractor on a large scale or a small subcontractor; the IT setup in your company is crucial. In that case, it should be compliant with DoD and NIST standards from the upper level to the ground level.
First, it is necessary to have a System Security Plan (SSP). This can provide you with a clear description of your security measures.
The plan is not just a security check; it is a detailed depiction of how you provide the necessary security for CUI! Regardless of the platform or device used.
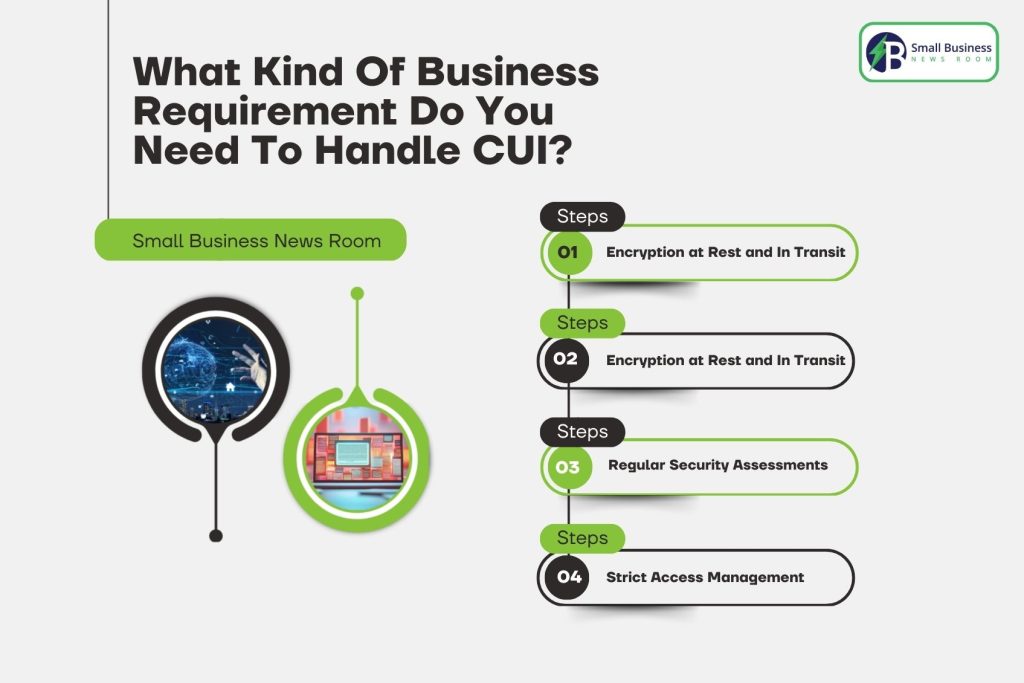
Also, your network needs to have:
- Encryption at Rest and In Transit: All Controlled Unclassified Information (CUI) data needs encryption when stored on servers and during transfer between systems.
- Encryption at Rest and In Transit: Data classified as CUI also requires encryption both when it is at rest on servers and during transfer between systems.
- Regular Security Assessments: Continuously running vulnerability scans along with penetration testing to uncover loopholes and areas of weakness before the attackers.
- Strict Access Management: There should be loimited access to the CUI for the individuals who absolutely require it, and need authenticate access through multi-factor authentication and robust password policies.
Even small businesses that are dealing with CUI cannot avoid the need for firewalls, endpoint security tools, and secure cloud services. It is not skipping these steps that is merely risky, but also noncompliant.
Read also: What Is The Goal Of Destroying CUI? Safeguarding Sensitive Data
Why Is It Necessary To Review The System Requirements Regularly?
Adherence to the CUI standards is not a one-time task! it is an ongoing project. Technology evolves, cyber threats become increasingly sophisticated, and they are continuously updating compliance.
A system that was secure two years ago may no longer meet current requirements. Regular reviews play a crucial role in identifying vulnerabilities.
Bad configurations, unsupported software, and missed security patches can become sources of cybercriminal intrusions.
For example, an unpatched server or a forgotten user account may be exploited by intruders to gain access to sensitive government data. This risk could result in your company incurring millions in fines and losing contracts.
Conducting routine reviews also allows you to prepare for audits. The Department of Defense is famous for requiring contractors to prove their compliance via formal assessments.
So, Keeping up to date means that you will not be caught off guard when an audit notice is received.
What Are The Best Practices For An Ongoing Review?
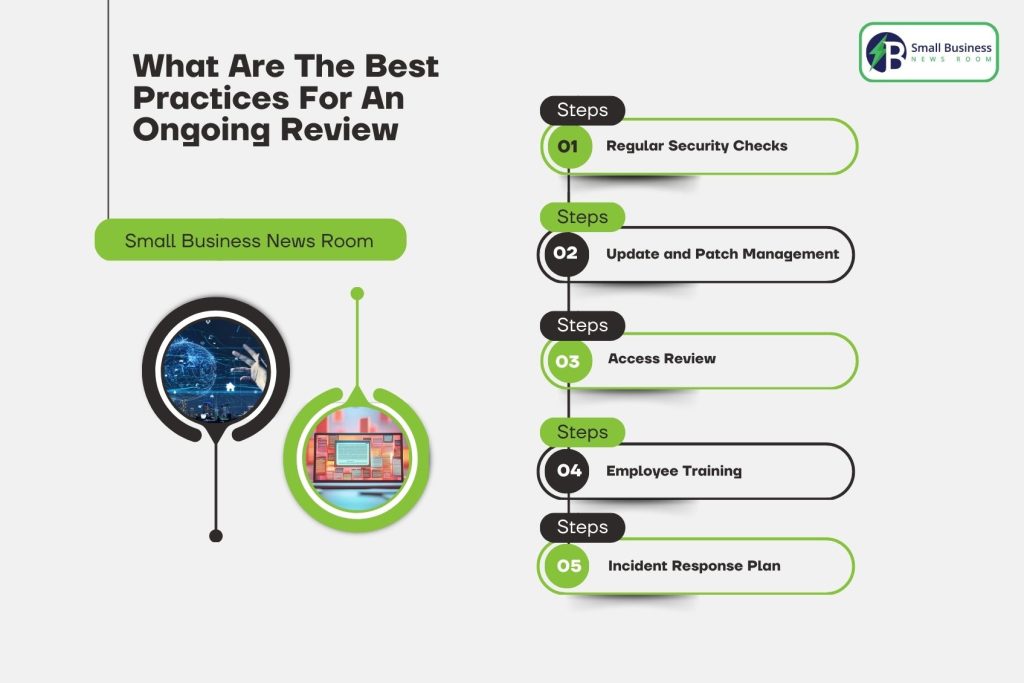
Continual care is crucial if you want your systems to remain CUI-ready. Here are a few best practices that you can consider:
Regular Security Checks: Conducting regular vulnerability scans, penetration tests, and configuration audits should be part of your security schedule. These activities allow you to detect problems at an early stage.
Update and Patch Management: Security against known exploits becomes stronger with the application of software and firmware updates.
Therefore, updates should never be postponed to the point where they are almost at the end of the release cycle.
Access Review: Reevaluation of user permissions is necessary. It helps ensure that current employees with a legitimate need can access CUI.
Employee Training: Oftentimes, people are the weakest link in the cybersecurity chain. Phishing awareness and adherence to security policies are the primary objectives of ongoing staff training.
Incident Response Plan: In the event of detecting, isolating, and reporting security breaches, you need to follow a well-prepared and tested plan.
With the help of periodic reviews and enhancements to your setups, you’ll be able to meet compliance requirements. This can further help to reduce the likelihood of a data breach, which could be very costly.